UNRAID - Restricting Docker External Access for Self-Hosted Containers and Access via Reverse Proxy
Table of Contents
Note: This doesn’t apply to only UNRAID, as it is just Docker configurations but I include steps for UNRAID. I won’t be going into creating a reverse proxy (There are plenty of tutorials out there for that but I recommend NGINX Proxy Manager if you are new)
If you self-host a lot of applications you may find that sometimes you worry about what happens if it is compromised. Maybe it’s an application that holds sensitive information such as a password manager you don’t want exposed except in your network (via VPN). The following will allow you to create a container with restrricted access (no internet or local access to the network except access from host)

Create LAN Only Docker Network #
Run the following command docker network create onlylocal --internal --subnet=172.44.0.0/16 where ‘onlylocal’ can be whatever you want to name the network, and subnet (required) is defined up to you.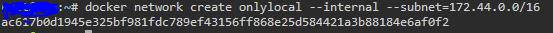
Apply LAN Only network to ‘sensitive’ container #
For demo purposes I will demonstrate the sensitive docker container you want to restrict with an nginx container in the basic template
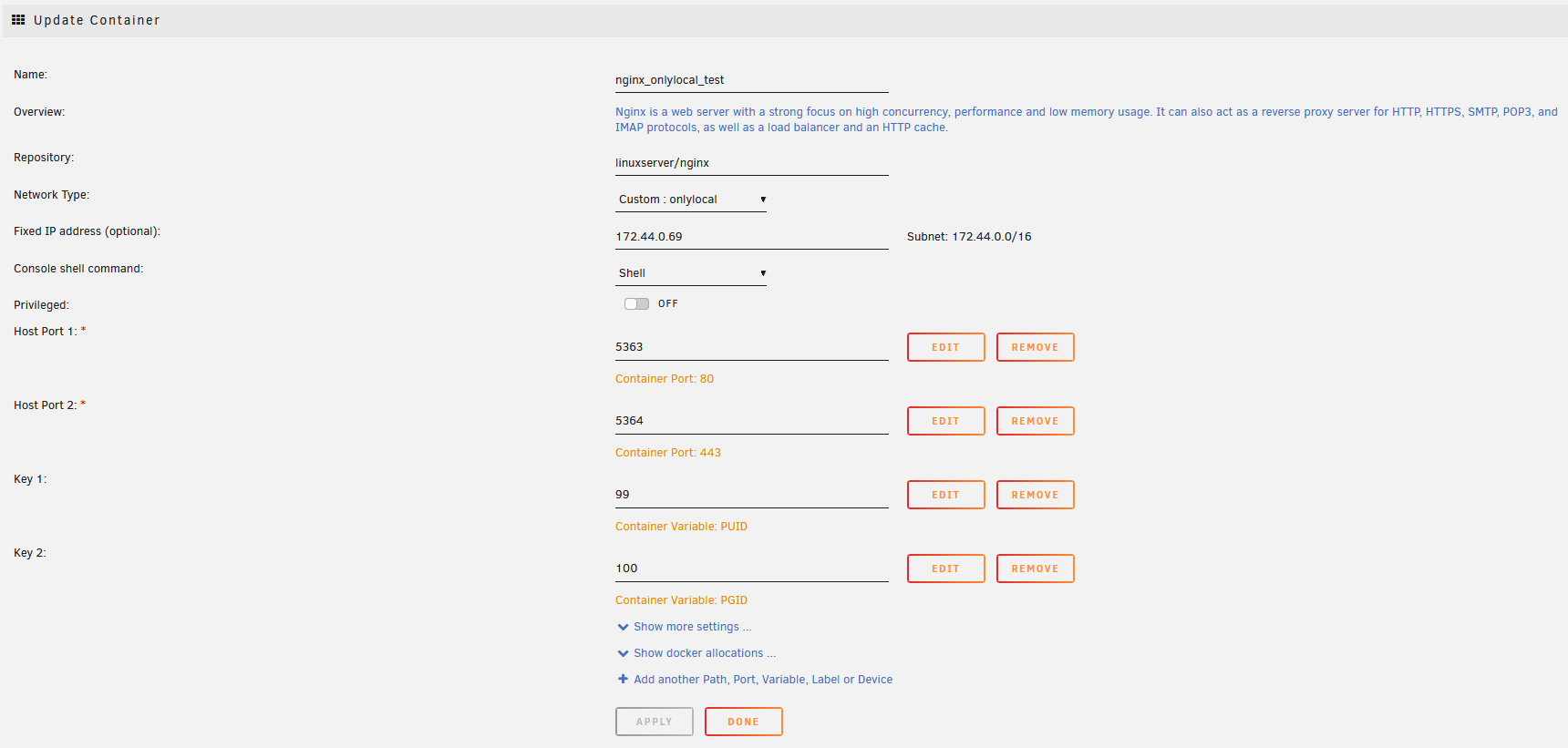
- Creating docker container (internal ip on network statically set to 172.44.0.69 here for demo)
- Running demo app
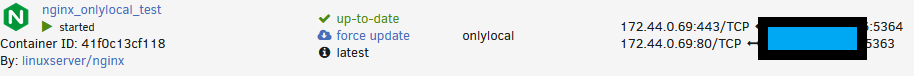
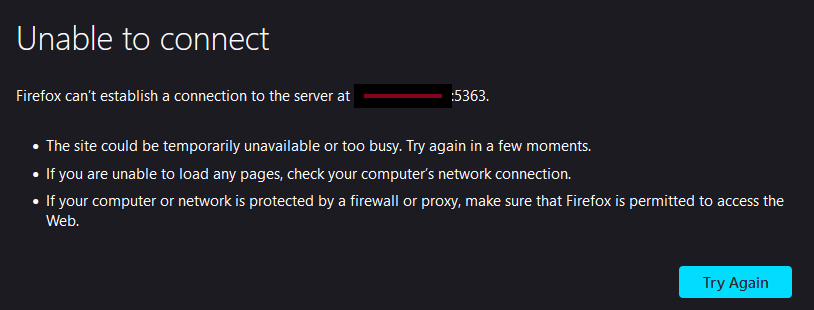
- Testing that we cannot access locally
Connect reverse proxy to access #
I recommend a custom DNS server for your network that points to the reverse proxy on a custom domain that you can only access on LAN
- In your reverse proxy container, add post arguments (Assuming UNRAID) to connect to the restricted network
; docker network connect onlylocal Nginx-Proxy-Manager-OfficialYou can replace ‘Nginx-Proxy-Manager-Official’ with whatever your reverse proxy container name is. - Configure reverse proxy to forward requests into the internal ip (in my case 172.44.0.69 as previously set for demo)
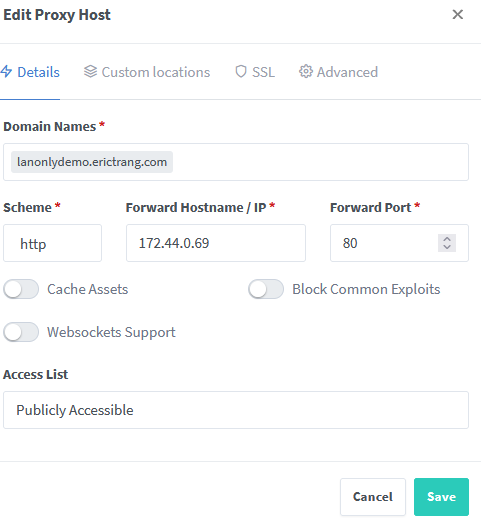
- ???
- Profit!
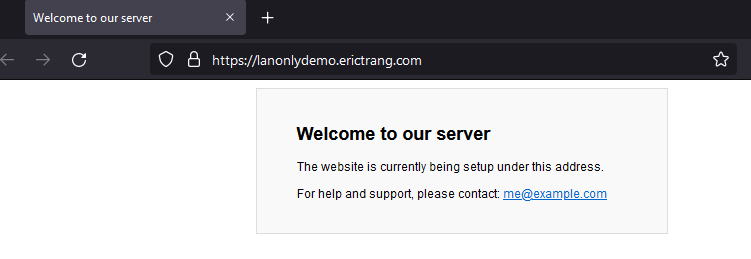
Now you can be sure your restricted app can only be accessed through your reverse proxy (with whatever configuration you make for your reverse proxy which I hope you secured!).